7.11.2 Hybrid encryption
A hybrid encryption scheme is a specific type of hybrid cryptosystem that allows Alice and Bob to securely encrypt data they want to exchange over an insecure communication channel. Figure 7.7 shows the architecture of a hybrid encryption scheme. It strongly resembles that of the hybrid cryptosystem and is composed of two parts:
- A public-key cryptosystem PKS used as a means to establish a shared secret key
- A symmetric-key encryption E used as a Data Encapsulation Method (DEM) to securely encrypt the actual (bulk) data using the newly established secret key [105].
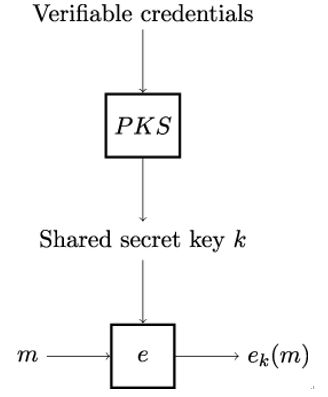
Figure 7.7: Architecture and working principle of hybrid encryption
Like with a general hybrid cryptosystem, shown in Figure 7.6, Alice and Bob first use the public-key cryptosystem to establish a shared secret key k. In the second step, they use a symmetric-key encryption e to encrypt plaintexts m under the key k.
A hybrid encryption system has the following cryptographic properties [105]:
- It ensures secrecy because Alice and Bob mutually verified their identities during the key agreement phase and therefore are the only communicating entities who know the shared secret key k. Alice and Bob can than use a symmetric key encryption e – for instance, the Advanced Encryption Standard (AES), which we will discuss in detail in Chapter 14, Block Ciphers and Their Modes of Operation – that is secure against polynomial time adversaries. Consequently, Eve is not able to extract any information about m from the ciphertext ek(m), except its length.
- It allows ubiquitous application because Alice and Bob can verify each other’s identity based on the credentials they present during the key agreement phase. As a consequence, Alice and Bob can securely establish a shared secret key even if they have never met each other before.
- The symmetric-key encryption e itself can be performed in ways that ensure randomization of the resulting ciphertexts. Randomization means that two identical plaintext messages m will yield two completely different ciphertexts. As a result, Eve has no way to determine whether a given plaintext corresponds to a specific ciphertext even if Eve knew one or more plaintexts that Alice or Bob encrypted.
Now let’s take a look at a specific example of a hybrid encryption scheme.
Leave a Reply